What Is Unified ID 2.0?
Unified ID 2.0 (UID 2.0) offers a privacy-centric, consent-based alternative to cookies, which enables identity resolution across different devices. As privacy regulations tighten and third-party cookies near their end in major browsers, there are significant challenges in maintaining effective, privacy-compliant targeting.
The adoption of UID 2.0 isn’t just about replacing cookies–it’s about improving transparency and control for users while enhancing the capabilities of advertisers and publishers. UID 2.0 prioritizes user consent and provides cross-device identification, allowing seamless tracking and targeting across different devices.
In this article we’ll delve deeper into what UID 2.0 is, how it works and how it compares to other identity solutions.
What Is Unified ID 2.0?
Unified ID 2.0 is a privacy-centric, alphanumeric identifier derived from a user’s email address or phone number. Unlike other identifiers, UID 2.0 is open-source and requires explicit user consent. Users must share their email address with a publisher to generate the unique identifier.
The creation of Unified ID 2.0 is led by The Trade Desk. However, the development of UID 2.0 involves collaboration with multiple industry partners, including ad tech companies, publishers, and data providers.
Cookies became indispensable in advertising because they were the industry standard, widely adopted by brands, publishers, and ad tech companies alike.
Now, Unified ID 2.0 is following a similar trajectory, rapidly gaining momentum across the ad tech ecosystem. Major players like Index Exchange, Magnite, PubMatic, OpenX, Criteo, and LiveRamp have embraced UID 2.0.
Note: Publishers like The Washington Post, and its Zeus technology platform are part of the growing UID community. Nielsen, a leader in media measurement, has made UID 2.0 a cornerstone of its enhanced measurement tools.
The framework is governed by the IAB Tech Lab, which oversees its privacy and security standards, although the IAB Tech Lab does not act as the administrator. The open-source nature of UID 2.0 allows contributions from other major companies–fostering a wide effort to create a cookie-independent identity solution.
Purpose of UID 2.0 in the advertising ecosystem
Unified ID 2.0 enables advertisers and publishers to reach users without relying on third-party data. It functions independently of third-party cookies, allowing for personalized ad targeting while maintaining consumer privacy.
In simple terms, UID2 offers a privacy-focused, cookie-independent alternative to third-party cookies.
UID 2.0 vs third-party cookies
UID 2.0 can offer improved user trust, better data security, and continued access to personalized advertising without the privacy risks associated with third-party cookies.
Third-party cookies often track users without explicit consent, but UID 2.0 requires users to provide their email address and consent to be identified. This gives greater transparency for users, and they can control their data sharing at any time.
Also, third-party cookies track users across the web, storing vast amounts of personal data, which can lead to privacy concerns. UID 2.0, on the other hand, encrypts and hashes email addresses, offering enhanced privacy protection.
With third-party cookies, tracking can connect users to specific behaviors or locations. UID 2.0 anonymizes user data, reducing the risk of real-world identification and allowing users to remain anonymous.
How does it differs from cookie-based identification?
| Aspect | Third-party cookies | UID 2.0 |
| Cross-site targeting | Enabled by default, tracking users across different websites | Requires user consent but allows cross-site targeting through encrypted identifiers |
| User control | Limited user control and difficult to opt-out | Users have greater control and can opt-out at any time |
| Consent and transparency | Passive tracking, often without explicit consent | Requires explicit user consent and email login |
| Privacy and security | Tracks user data across multiple sites, raising privacy concerns | Encrypts and hashes user data, offering enhanced privacy |
| Anonymity | Can expose personally identifiable information | Ensures user anonymity through encryption and regularly updated identifiers |
| Data source | Relies on data collected from various third-party sources | Relies on first-party data directly provided by users |
Why does UID 2.0 matter for industry-wide adoption?
The main point is that UID 2.0 offers a privacy-compliant, cookie-independent solution.
Publishers and advertisers are able to maintain personalized ads through first-party data while ensuring users’ privacy with encrypted, consent-based identifiers. UID2’s open-source nature fosters interoperability across platforms, making it easier for publishers to integrate without extensive costs.
How Does Unified ID 2.0 Work?
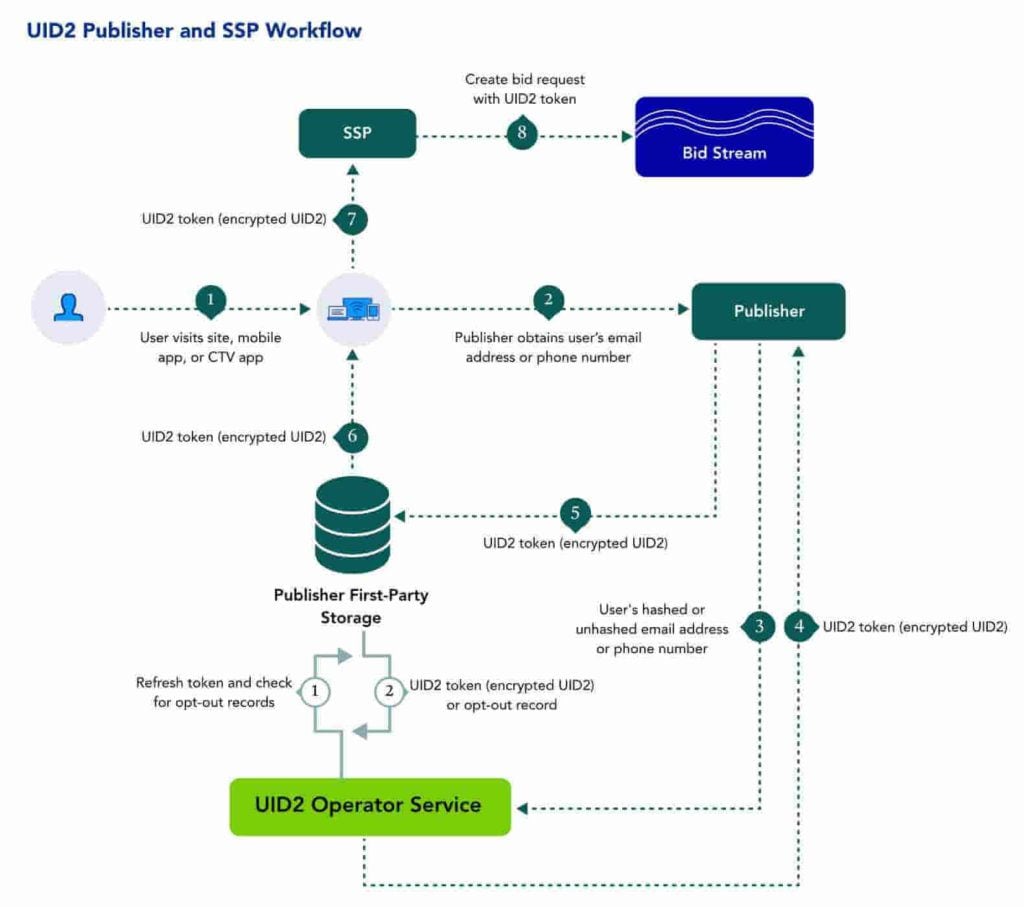
Here’s a simple 5 step breakdown of how UID 2.0 works:
- Users visit a website, CTV, or mobile app and log in using their email address. The website asks for the user’s consent to use their data, explaining the value exchange (e.g., access to content in exchange for personalized ads).
- The user’s email is encrypted (hashed and salted) to create a unique identifier. This process ensures that the email remains secure and anonymous.
The user is given control over their data-sharing preferences. They can adjust privacy settings and choose how their information is used.
- A unique UID 2.0 token is created and sent back to the publisher. The identifier is regularly updated to enhance security.
- The publisher shares the UID 2.0 token with SSPs for real-time bidding. No personal information is shared in this process.
- DSPs decrypt the UID 2.0 token during ad auctions to match it with relevant audience data and deliver targeted ads.
Note: If the user visits another site within the UID 2.0 network, they are automatically logged in, creating a smooth experience across multiple platforms. If the user decides to opt out, the UID 2.0 administrator communicates this to all relevant platforms, ensuring the user’s privacy is respected.
Source: Unifiedid
What Makes UID 2.0 Different From Previous Identity Solutions?
UID 2.0 uses deterministic data, such as a user’s email address or phone number, to create a unique, hashed, and encrypted ID. Thus, advertisers and adtech companies can identify users across websites and devices without exposing personal information.
What sets UID 2.0 apart from previous solutions is its ability to function across multiple environments–web browsers, mobile apps, and connected TVs. By Integrating device graphs, it can match identifiers generated in one environment (e.g., a web browser) with those from another (e.g., mobile devices), creating a unified view of the user.
Unlike many previous identity solutions that operated within isolated environments, UID 2.0 provides a more transparent and privacy-centric approach.
Privacy-centered approach
One of the biggest criticisms of cookies, which is why they are being phased out, is their lack of privacy protections. Cookies track users across the web without transparent consent.
UID 2.0 addresses these privacy issues by requiring users’ explicit consent and creating a more secure, privacy-centric identification system. It allows users to decide how their data is used, aligning with the latest privacy standards.
Pseudonymization
A user’s UID 2.0 identifier is a random string of letters and numbers encrypted and hashed, meaning it cannot be reverse-engineered to reveal personal information. This system provides enhanced privacy, ensuring that even if a UID 2.0 is intercepted, it cannot be linked back to a real person.
Additionally, there is no centralized database that maps UID 2.0s to real-world identifiers, further protecting users from potential data breaches.
Transparency and control for users
Transparency is a cornerstone of UID 2.0.
UID 2.0 requires users to log in with their email and consent to data sharing. Through this login, users can access a dashboard where they can monitor their data, adjust privacy settings, and opt out at any time.
When users opt in, publishers and advertisers can offer a more personalized experience. This is communicated clearly to users so they understand the value exchange and that their data helps fund free access to content or services through targeted advertising.
Unlike cookies, where this exchange was often unclear or hidden, UID 2.0 makes it straightforward, building user trust and improving transparency.
Benefits of Unified ID 2.0 for Publishers
Here are 4 main benefits for publishers integrating with UID2:
- Seamless audience targeting across desktop, mobile, and CTV devices using a single identifier, which improves the reach and accuracy of campaigns.
- Consistent frequency management across devices that reduces overexposure to the same ads and improves user experience.
- Improved content recommendations and personalized ad experiences, which can lead to higher user engagement and retention.
- More control to users over their data, including the ability to easily opt-out. This transparency builds trust with users, improving long-term relationships.
How Does UID 2.0 Improve Monetization for Publishers?
Higher CPMs
By providing more relevant and personalized ads through cross-device targeting, publishers can command higher CPMs. Buyers are willing to pay more for impressions that come with higher targeting precision and user engagement.
Independence from cookies
Since UID 2.0 does not rely on third-party cookies, publishers can continue to monetize inventory across browsers that have already restricted cookies (e.g., Safari, Firefox), helping to future-proof their ad revenues.
Openness and collaboration
UID 2.0 is built on an open-source framework, making it interoperable with other IDs and systems. This openness encourages collaboration with various partners in the ad tech ecosystem, driving more bids and improving overall monetization potential.
Enhanced audience targeting
The deterministic, consent-based approach of UID 2.0 enables better audience targeting.
This means advertisers can target users more precisely across multiple devices while maintaining user privacy. But publishers can get higher-quality impressions, as advertisers can reach specific audience segments more effectively.
UID 2.0 allows advertisers to combine their first-party data with its identity framework. Thus, advertisers can create a more comprehensive view of their audience by linking their first-party data (e.g., CRM or email data) with UID 2.0’s encrypted identifiers.
How does better targeting improve ad revenue?
Better targeting ensures that ads are shown to the most relevant audience segments, which boosts engagement and conversion rates. When users see ads that align with their interests, they are more likely to interact with them, leading to higher CTRs. This drives advertisers to bid more for well-targeted impressions, also leading to higher CPMs for publishers.
Additionally, better targeting reduces wasted ad spend, as advertisers avoid showing ads to uninterested users.
How can small publishers benefit from UID 2.0?
Small publishers gain access to the same advanced identity resolution technology used by larger media companies. With better targeting capabilities, small publishers can increase their CPMs, attract more demand from advertisers, and reduce reliance on third-party cookies.
Unified ID 2.0 vs Other Identity Solutions
Here are examples of other identity solutions in the ad tech ecosystem:
| Identity solutions | Purpose |
| Google Privacy Sandbox | Google’s Privacy Sandbox initiative aims to offer privacy-compliant ad targeting and measurement by replacing cookies with solutions like FLoC (Federated Learning of Cohorts) and Topics API, which group users into interest categories without tracking individuals. |
| SWAN (Secure Web Addressability Network) | SWAN is another privacy-focused solution similar to UID 2.0 but with a decentralized model. It allows publishers and consent management platforms to generate pseudonymous identifiers for tracking users across websites. |
| ID5 | ID5 is a universal identity solution that enables addressable advertising without third-party cookies. It supports cross-channel targeting and is used in programmatic advertising. It can leverage both deterministic and probabilistic data to create user IDs. |
| LiveRamp RampID (ex., IdentityLink) | This solution connects offline and online data using a deterministic matching process. It helps brands and advertisers match users across devices and channels while protecting user privacy through anonymization |
| SharedID (Prebid) | SharedID is an open-source solution that enables cookie-less identity resolution by providing users with a unique identifier, designed to be transparent and privacy-compliant. It’s widely adopted within the Prebid community and serves as an alternative to traditional cookie-based IDs. |
| The NetID Foundation | Based in Europe, NetID is an open login standard that provides users with a single login for multiple websites. It focuses on data privacy and transparency, with support for publishers and advertisers needing an alternative to third-party cookies. |
Unified ID 2.0 vs. Google’s Privacy Sandbox
Unified ID 2.0 and Google’s Privacy Sandbox are both designed to address the impending end of third-party cookies, but they take significantly different approaches to privacy, user tracking, and ad targeting.
UID 2.0 focuses on preserving individual-level targeting while maintaining privacy and transparency through consent, while Google’s Privacy Sandbox moves away from individual-level targeting. Instead, it groups users into cohorts based on shared browsing behaviors using tools like the Topics API.
It’s designed to protect privacy by ensuringthat users are not individually tracked across the web. While Privacy Sandbox focuses on interest-based targeting (via cohorts) and contextual advertising, it prioritizes user anonymity over personalized, individual ad targeting.
The system is built into Google Chrome, making it reliant on the browser environment rather than individual identifiers.
A look at alternatives like LiveRamp’s IdentityLink and Lotame Panorama ID
Let’s check out two more identity solutions:
- LiveRamp’s RampID (formerly–IdentityLink) is another widely adopted solution for ID resolution. It connects offline and online data by linking users’ identities across devices, platforms, and environments using deterministic matching, typically based on email addresses or phone numbers.
RampID anonymizes and encrypts data to maintain privacy and security, similar to UID 2.0. Both advertisers and publishers widely use it to enable cross-channel targeting, improve measurement, and create a people-based marketing approach.
- Lotame’s Panorama ID focuses on people-based identity using deterministic, probabilistic, and behavioral data. Unlike UID 2.0, which primarily relies on deterministic data, Panorama ID creates audience profiles by aggregating data from multiple sources.
This also provides advertisers with cross-channel reach across different devices while maintaining privacy. Panorama ID is designed to function without third-party cookies, offering a flexible and scalable alternative for publishers and advertisers.

Why may some businesses choose a different solution?
Some businesses may opt for alternatives to UID 2.0 because it relies heavily on deterministic data, which may not suit all companies, especially those without robust first-party data collection.
Solutions like Google’s Privacy Sandbox or LiveRamp’s RampID may appeal more to businesses prioritizing group-based targeting or probabilistic methods that don’t require users to log in with personal details.
Additionally, some companies might favor solutions integrated with their existing tech stacks or privacy frameworks, offering different compliance or scalability options depending on their operational needs.
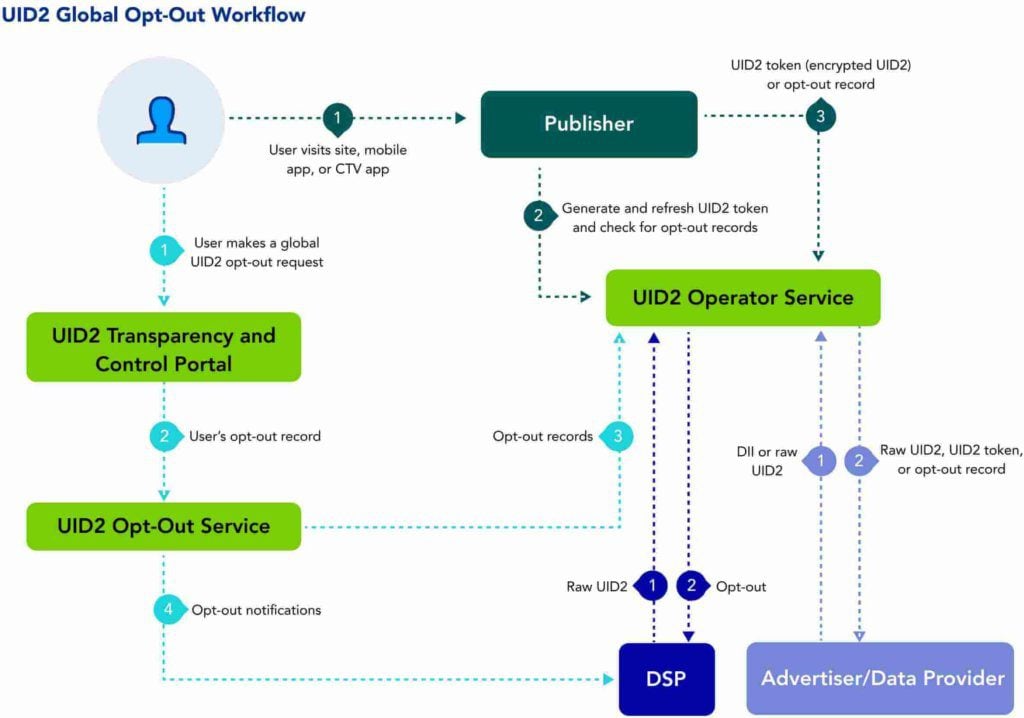
Unified ID 2.0 and Consumer Privacy
How does UID 2.0 give users control over their data?
UID 2.0 gives users greater control by requiring explicit consent before generating a unique identifier based on their email or phone number.
Users can adjust their privacy preferences anytime, including the ability to opt out of data tracking or delete their data entirely. Meaning–users are actively involved in how their personal information is used, enhancing transparency and trust.
Transparency for the end user
Consent is central to UID 2.0’s privacy framework. Before any data is collected or used, users must give permission. Users also retain data rights, including the ability to view, modify, or delete their personal data.
What do users see when they opt-in to UID 2.0?
When users opt-in to UID 2.0, they are presented with a clear explanation of the value exchange.
- For example, that their data will be used to provide personalized ads in exchange for free access to content.
Users are informed about how their data will be anonymized and secured, and they can customize their privacy settings, such as choosing what data to share and with whom.
Source: Unifiedid
How does UID 2.0 handle sensitive data?
As we’ve already mentioned, UID 2.0 uses encryption, hashing, and salting techniques to protect personally identifiable information.
- When a user provides their email, UID 2.0 transforms this into an anonymized, pseudonymous identifier through hashing and adding a rotating salt, making it impossible to reverse-engineer or trace back to the original data.
Additionally, UID 2.0 does not store any PII in centralized databases. Instead, the data remains encrypted throughout the ad ecosystem, and users can control how their data is used.
How to Implement Unified ID 2.0 as a Publisher?
1. Request access to UID 2.0
Start by filling out the Request Access form on the official UID 2.0 website.
This form is required to begin the process and gain entry to the necessary tools and documentation. Ensure all your team members who will be involved in the integration are aware of this step.
2. Identify properties for integration
Determine the specific websites, mobile apps, or CTV platforms where you want to implement UID 2.0.
Identifying these properties early allows you to plan the integration more effectively and ensures that you cover all relevant platforms. Each property will need to support UID 2.0 tokens for audience targeting and monetization.
3. Sign the UID 2.0 contract
Once your application is approved, you must sign a contract to officially participate in the UID 2.0 framework. This contract outlines your responsibilities as a publisher, including compliance with privacy regulations and data handling practices.
4. Choose your integration type
Decide between client-side, client-server, or server-side integration based on your infrastructure. Each method has its own advantages:
- Client-side: Easier to implement and suitable for smaller publishers.
- Client-server: A balanced option for those with moderate technical resources.
- Server-side: Offers greater control and customization but requires more technical effort.
Inform your UID 2.0 contact of your chosen integration type so they can provide the appropriate documentation and support.
5. Review Integration Approaches
For detailed guidance on how to integrate UID 2.0, refer to the Integration Approaches section.
This section provides specific steps based on your chosen method, including setup instructions for web, mobile, and CTV environments.
6. Obtain UID 2.0 credentials
Once the contract is finalized, you will receive UID 2.0 credentials. These are essential for generating UID 2.0 tokens and authenticating your integration with the UID 2.0 system.
7. Build the integration
Using the credentials, begin building your integration. You can either use an SDK provided by UID 2.0 or directly integrate with the UID 2.0 APIs.
- The SDK simplifies the token generation process, while the API allows for more direct integration with your system. Ensure that all communications between your servers and UID 2.0 are encrypted to protect user data.
8. Test the implementation and go live
Before going live, test your implementation to ensure that UID 2.0 tokens are being generated, passed, and decrypted properly in RTB requests. Work with your SSPs to troubleshoot any issues during this phase.
Ensure that the tokens flow correctly through the bidstream. After successfully testing, you are ready to launch UID 2.0 on your platform!.
Integration with the existing ad tech stack
To implement Unified ID 2.0, publishers must ensure compatibility with their existing ad tech stack.
This typically involves integrating UID 2.0 with your CMS and ad server to replace third-party cookie-based identifiers. The integration process can be streamlined by partnering with platforms and vendors already supporting UID 2.0, such as ad exchanges or SSPs that are part of the UID 2.0 ecosystem.
Compatibility with demand-side platforms (DSPs) and supply-side platforms (SSPs)
UID 2.0 is designed to work across the broader ad tech ecosystem, ensuring compatibility with both DSPs and SSPs.
Publishers must collaborate with SSPs supporting UID 2.0, enabling the identifier to be passed through the ad bid stream securely. This ensures that DSPs can decrypt the UID 2.0 token and use it to target users across different devices and environments.
Note: before full-scale implementation, publishers should confirm that their SSP partners are actively participating in the UID 2.0 ecosystem and that DSPs in their network can recognize and work with the encrypted identifiers.
Potential Challenges in Implementation of Unified ID 2.0
UID 2.0 offers a privacy-compliant alternative to cookies, but there are technical hurdles, reliance on first-party data, user consent, and regulatory compliance, that present challenges which should be carefully managed.
1. Technical integration
Integrating UID 2.0 with existing systems, such as content management systems, ad servers, and SSPs, requires technical expertise and resources. Publishers must modify their infrastructure to support UID 2.0 tokens, which may involve significant development and testing.
2. First-party data requirements
UID 2.0 heavily relies on first-party data, which may pose a challenge for companies that don’t have robust first-party data collection strategies. Businesses without strong customer relationships or direct login systems might struggle to gather enough data for UID 2.0 to be effective.
3. User adoption and consent
Obtaining explicit user consent is crucial for UID 2.0, but convincing users to opt-in and share their email or phone number may be difficult, especially for sites where users aren’t accustomed to logging in.
This could limit the scale of UID 2.0 adoption and reduce its effectiveness compared to cookies.
The Role of Unified ID 2.0 in Programmatic Advertising
As third-party cookies are phased out, UID 2.0 helps maintain the personalized, data-driven advertising capabilities that advertisers and publishers rely on, while adhering to stricter privacy regulations like GDPR and CCPA.
Its open-source and interoperable design makes it widely adoptable, providing a common framework for addressing identity across digital advertising.
Connecting buyers and sellers in a privacy-first world
UID 2.0 helps to create seamless connections between advertisers (buyers) and publishers (sellers) by enabling them to target users with personalized ads while respecting their privacy preferences.
The identifier is generated with explicit user consent, ensuring compliance with privacy laws, and passed along the ad supply chain in a hashed and anonymized format. Thus, DSPs and SSPs can work together effectively, enhancing the relevance of ads shown to users.
How are DSPs and SSPs adopting UID 2.0?
Major DSPs like The Trade Desk and SSPs such as Magnite, PubMatic, and OpenX have already adopted UID 2.0. These platforms now pass UID 2.0 tokens in real-time bidding auctions, ensuring a higher bid accuracy for advertisers, while enabling publishers to better monetize their inventory.
Conclusion
Unified ID 2.0 is a vital solution that addresses the demand for privacy compliance while maintaining the effectiveness of personalized advertising. Its open-source, interoperable framework has garnered widespread support from significant ad tech platforms like The Trade Desk, signaling a broad industry shift towards privacy-first, identity-driven advertising.
For publishers and advertisers, adopting UID 2.0 is key to delivering personalized ads while respecting users, ensuring sustainable, transparent and effective monetization.
Frequently Asked Questions about Unified ID 2.0 (FAQs)
What makes Unified ID 2.0 different from other identity solutions?
UID 2.0 focuses on user consent and privacy by using encrypted, anonymized identifiers, and operates across devices without relying on third-party cookies.
How can publishers benefit from adopting UID 2.0?
Publishers can offer personalized advertising, improve cross-device targeting, and maintain compliance with privacy regulations, all while increasing their ad revenue potential.
Is Unified ID 2.0 compliant with GDPR and CCPA?
Yes, UID 2.0 is designed to be fully compliant with privacy regulations such as GDPR and CCPA by requiring explicit user consent and offering transparency around data usage.
What challenges might companies face when implementing UID 2.0?
Companies may face technical challenges in integrating UID 2.0 with their existing ad tech stack and ensuring compatibility with all partners in the ecosystem.
How does UID 2.0 protect consumer data?
UID 2.0 encrypts and hashes user data, ensuring it cannot be reverse-engineered, and provides users with full control over their privacy settings and opt-out options.